|
SAML(Security Assertion Markup Language) is an open standard for exchanging authentication information between an identity provider (IdP) and a service provider (SP). That means that you can use one set of credentials to log into many different websites, and to accomplish web browser single sign-on (SSO).
The authentication moment is the moment when the request enters the service framework. That means that a service always needs credentials.
If the Session expiration seconds field of the connection used to connect to the rule service has a value bigger than 0, then a session is created on the server side, and the client gets a SAML authentication cookie in the response. With this cookie, the client can connect again and use the same server session.
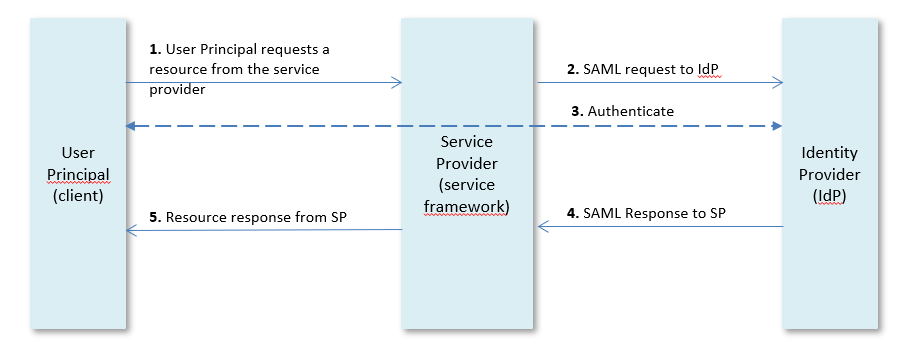
In a SAML login process there are three roles:
•The user principal (client) that requests a resource from the service provider (service framework) and provides an unique attribute (e.g. e-mail address) as user name. •The service provider (SP) redirects the user principal to the identity provider (IdP) for authentication. •The identity provider (IdP) validates the credentials and if valid the identity provider creates a SAML response assertion for the service provider. The user principal has now access to the resource.
|
| 1. | In Service Definer, open the window for the service for which you want to specify SAML authentication. |
| 2. | Set the Annotation attribute of the service to : |
@AuthSaml("entity-name")
| where entity-name is a valid entity name of a SAML Security Configuration. When using a connection to the rules engine for this service, the connection session name must be the same as the SAML configuration entity name. |
NOTE: You can also explicitly set SAML authentication on an individual method of the service. Do this by setting the Annotation attribute of that method to :
@AuthSaml("entity-name").
NOTE: You can also use
@AuthSaml(entity="<entity name>")
and in this case the session name of the connection used in the service may have any value. This allows multiple connections in a service using the same SAML configuration.
|
| 1. | In Service Definer open the server window that needs SAML authentication. |
| 2. | On the Security tab select a value for the Default Security Configuration from the list. All services that do not have another authentication annotation will use SAML authentication with this configuration. |
NOTE: You can also overwrite a method in a service that uses a different authentication mechanism than SAML, by explicitly setting SAML authentication on a service method. You can set Annotation attribute of the method to
@AuthSaml
with no parameters, and in this case the default SAML configuration set on the server is used.
|
See also
Authentication
Authentication matrix
|
